42 security labels access control
Access Control Security Software - Data Classification | Janusnet E-discovery tools can embed Janusseal security classifications directly into files and documents. Following classification, data governance or access control solutions can use the meta data in the file or document to allow/disallow access as required, matching the security classification label with the security clearance of the user. Security: Access Control - Bosch Security and Safety Systems I Global When trying to access the Access Easy Controller via Microsoft Edge, Chrome or other web browsers, you may get an error, "the connection for this site is not secure", which prevents you from connecting to the AEC. No ratings. 417. 0. 03-30-2022.
Oracle Label Security Oracle Label Security uses row level data classifications to enforce access controls restricting users to only the data they are allowed to access. It enables organizations to control their operational and storage costs by enabling data with different levels of sensitivity to co-mingle within the same database.
Security labels access control
Label-based access control Security labels are objects applied to rows and columns in order to protect these data, and granted to users to give them access to protected data. Protecting tables at row and column levels Protect rows and columns by associating them with security objects by including clauses in the CREATE TABLE and ALTER TABLE statements. Exemptions Control external access to resources in Azure Active Directory with ... In this article. Sensitivity labels help you control access to your content in Office 365 applications, and in containers like Microsoft Teams, Microsoft 365 Groups, and SharePoint sites. They can protect your content without hindering your users' collaboration and production abilities. Sensitivity labels allow you to send your organization's content across devices, apps, and services ... Define access control list and capability list and compare them ... The Discretionary Security Property: use of an access matrix to specify the discretionary access control. SE Linux, like most other systems that protect multi-level data, uses the BLP model. This model specifies how information can flow within the system based on labels attached to each subject and object.
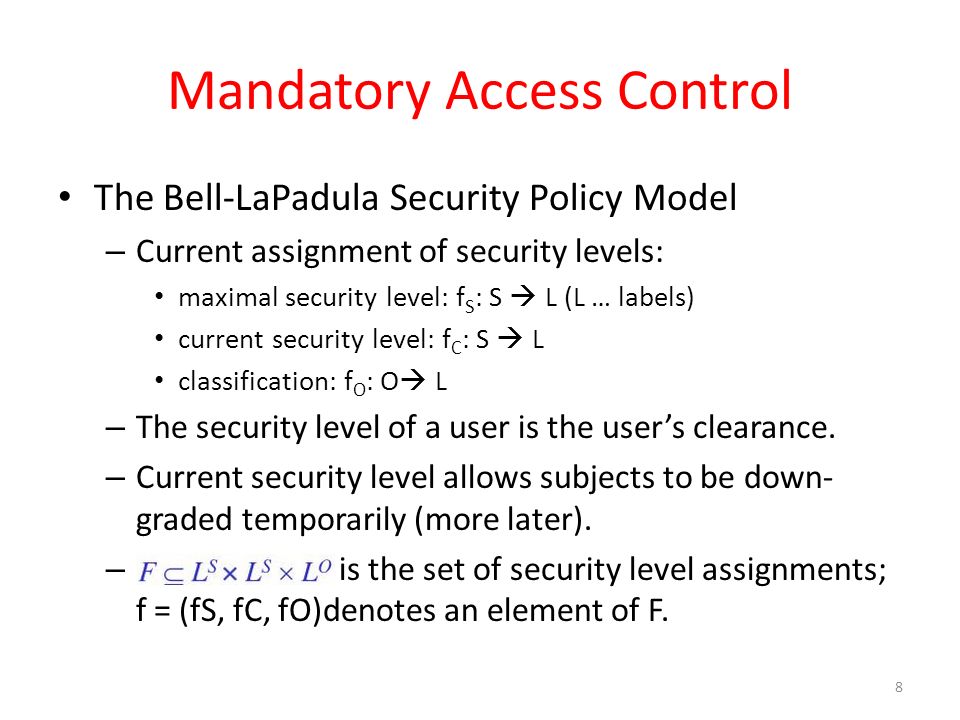
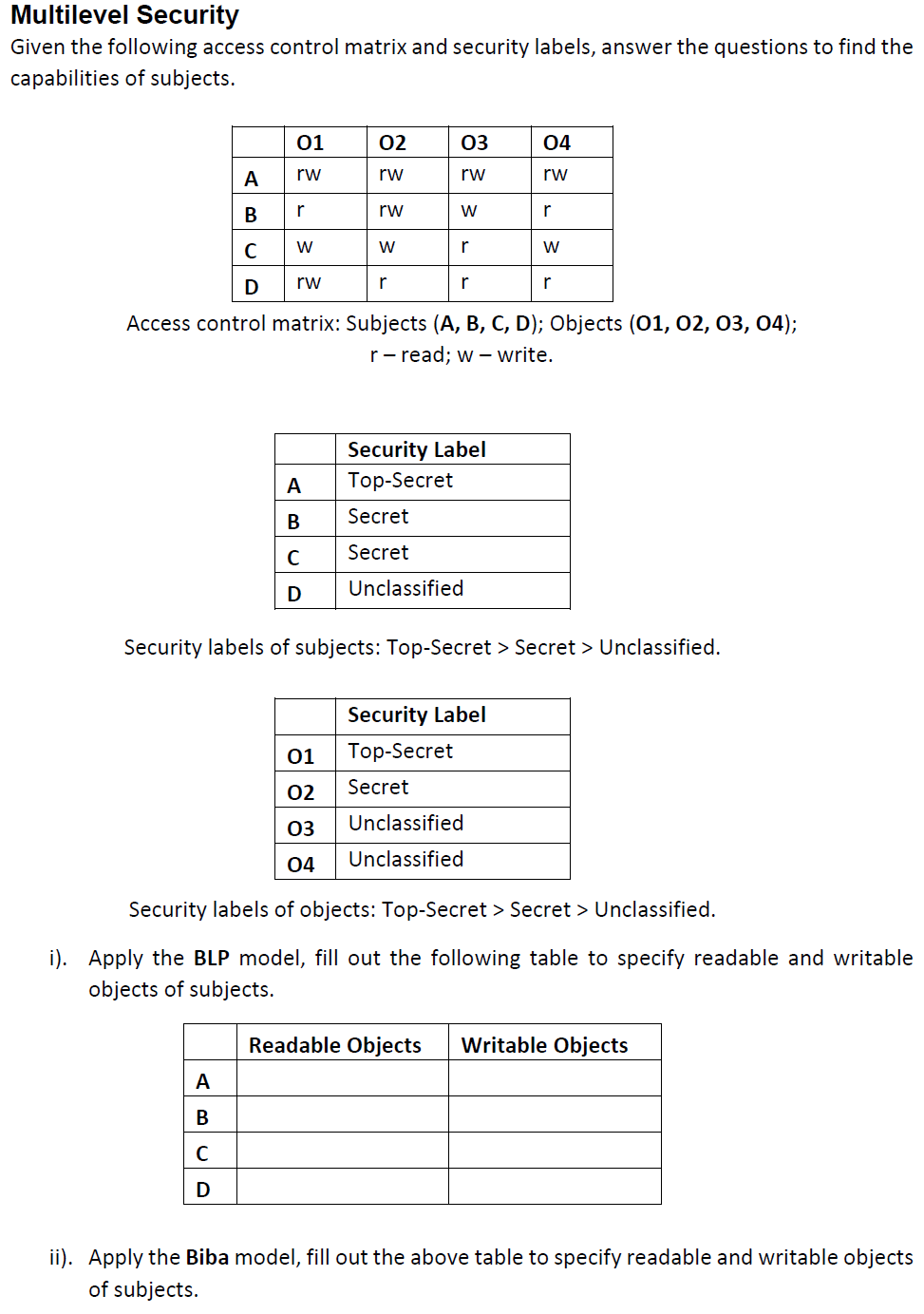
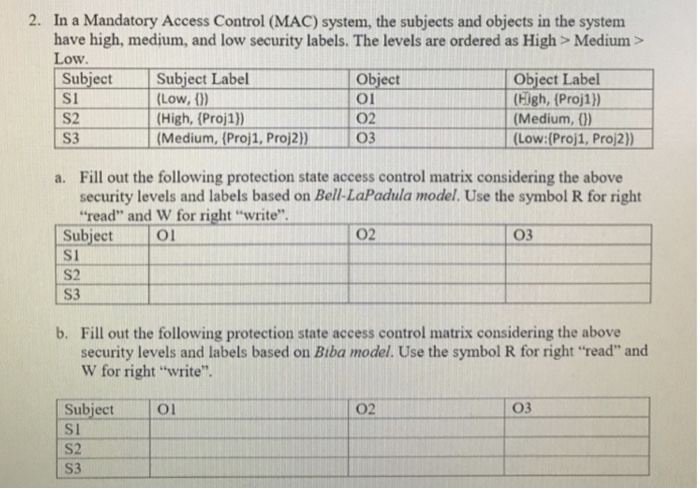
Security labels access control. 8 Access Control Models - Strengths, Weaknesses, and More Which brings us to our next model of access control - read on. Mandatory Access Control (MAC): the Secure Model Under mandatory access control (MAC), security administrators set access labels for both users and objects. Mandatory access control is the most secure of the major access control models, and also the most demanding to maintain. Mandatory Access Control - an overview | ScienceDirect Topics Mandatory Access Control ( MAC) is system-enforced access control based on subject's clearance and object's labels. Subjects and objects have clearances and labels, respectively, such as confidential, secret, and top secret. A subject may access an object only if the subject's clearance is equal to or greater than the object's label. Mandatory access control - Wikipedia Access to the labels and control mechanisms are not [citation needed] robustly protected from corruption in protected domain maintained by a kernel. The applications a user runs are combined with the security label at which the user works in the session. Access to information, programs and devices are only weakly controlled [citation needed]. A Unified Attribute-Based Access Control Model Covering DAC ... - Inria objects. Appropriate attributes can capture identities and access control lists (DAC), security labels, clearances and classi cations (MAC) and roles (RBAC). As such ABAC supplements and subsumes rather than supplants these currently dominant models. Moreover any number of ad-ditional attributes such as location, time of day, strength of ...
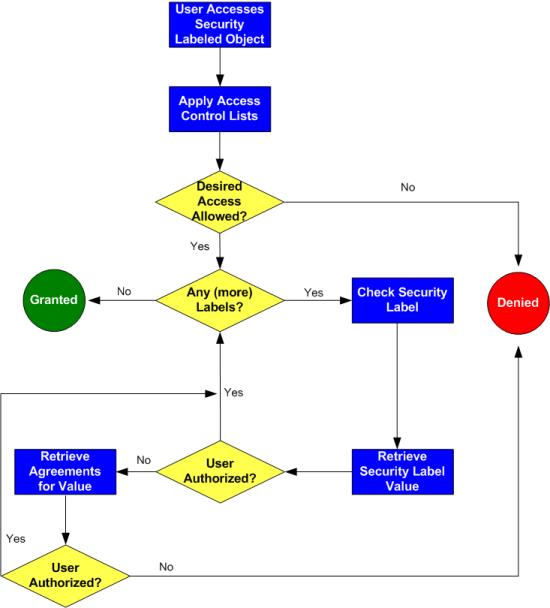
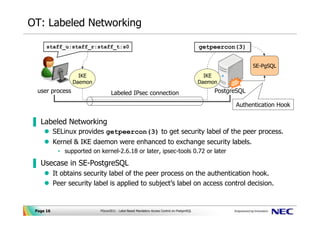
Label-based access control (LBAC) overview - IBM In label-based access control (LBAC) a security label is a database object that describes a certain set of security criteria. Security labels are applied to data in order to protect the data. They are granted to users to allow them to access protected data. Format for security label values PostgreSQL: Documentation: 14: SECURITY LABEL PostgreSQL places no restrictions on whether or how a label provider must interpret security labels; it merely provides a mechanism for storing them. In practice, this facility is intended to allow integration with label-based mandatory access control (MAC) systems such as SELinux. Such systems make all access control decisions based on object ... Access control: Models and methods in the CISSP exam [updated 2022] Access control and the CISSP certification. Access control is a core concept in cybersecurity, so naturally, it's covered on the CISSP certification exam.CISSP domain 5 covers identity and access management, and objective 5.4 within that domain is "Implement and manage authorization mechanisms."There are six main types of access control models all CISSP holders should understand: Access Control using Security Labels & Security Clearance - Isode Security Labels and Security Clearance provides a mechanism for controlling access to information that works well for large numbers of users. It can be an effective approach for access control in organizations that do not use non-electronic security labels. The following diagram shows the translation of the earlier example into electronic form.
Setting Access Control Permissions for Agreement Managers - PTC Read permission is required to access any object and view its information page. The following table illustrates additional access control permissions required for actions often completed by an agreement manager. The object location column has the following values. Use these values to determine the domain in which to grant access control ... Contact security - Oracle Contact security, also known as Label-Based Access Control (LBAC), allows you to use labels to manage access to contacts in your database. Note: Contact security is part of the Oracle Eloqua Security Administration Cloud Service and is included in the Standard and Enterprise trims. Mandatory Integrity Control - Win32 apps | Microsoft Learn Integrity labels specify the integrity levels of securable objects and security principals. Integrity labels are represented by integrity SIDs. The integrity SID for a securable object is stored in its system access control list (SACL). The SACL contains a SYSTEM_MANDATORY_LABEL_ACE access control entry (ACE) that in turn contains the integrity ... Access Control Models - UHWO Cyber Security - University of Hawai'i ... MAC uses "security labels" to assign resource objects on a system. There are two pieces of information connected to these security labels: classification (high, medium, low) and category (specific department or project - provides "need to know"). Each user account is also assigned classification and category properties.
Access Control Models: MAC, DAC, RBAC, & PAM Explained MAC works by applying security labels to resources and individuals. These security labels consist of two elements: Classification and clearance — MAC relies on a classification system (restricted, secret, top-secret, etc.) that describes a resource's sensitivity. Users' security clearances determine what kinds of resources they may access.
[Knowledge Hub] Windchill PLM Permissions/Access Control/Security Label How to set up security labels? How to troubleshoot access control issues? Log in eSupport Login: Close: Username (Email Address) Password; Invalid username or password Cancel: Forgot password? Create a new account: Support ... Windchill PLM Permissions/Access Control/Security Label Modified: 24-Aug-2022 Applies To Windchill PDMLink 10.0 to 12.0 ...
Security - FHIR v4.0.1 - Health Level Seven International The FHIR specification assumes that a security system exists, and that it may be deployed in front of or behind the FHIR API. The security system includes the following subsystems: Authentication: identifies and authenticates the user. Access Control decision engine: decides whether FHIR operations are allowed.
Mandatory Access Control: How It Works - Firewall Times Mandatory access control relies on a system of security labels. Every resource under MAC has a security classification, such as Classified, Secret, and Top Secret. Likewise, every user has one or more security clearances. To access a given resource, the user must have a clearance matching or exceeding the resource's classification.
Security Labels Overview - PTC Uniquely configured by each site, security labels work with the Windchill access control policies and ad hoc permissions for an object to determine whether a user is authorized to access an object. A site can configure multiple security labels to cover various needs, such as identifying legal information, establishing export control criteria, or protecting proprietary information.
Security-labels - FHIR v4.3.0 - Health Level Seven International A security label is a concept attached to a resource or bundle that provides specific security metadata about the information it is fixed to. The Access Control decision engine uses the security label together with any provenance resources associated with the resource and other metadata (e.g. the resource type, resource contents, etc.) to
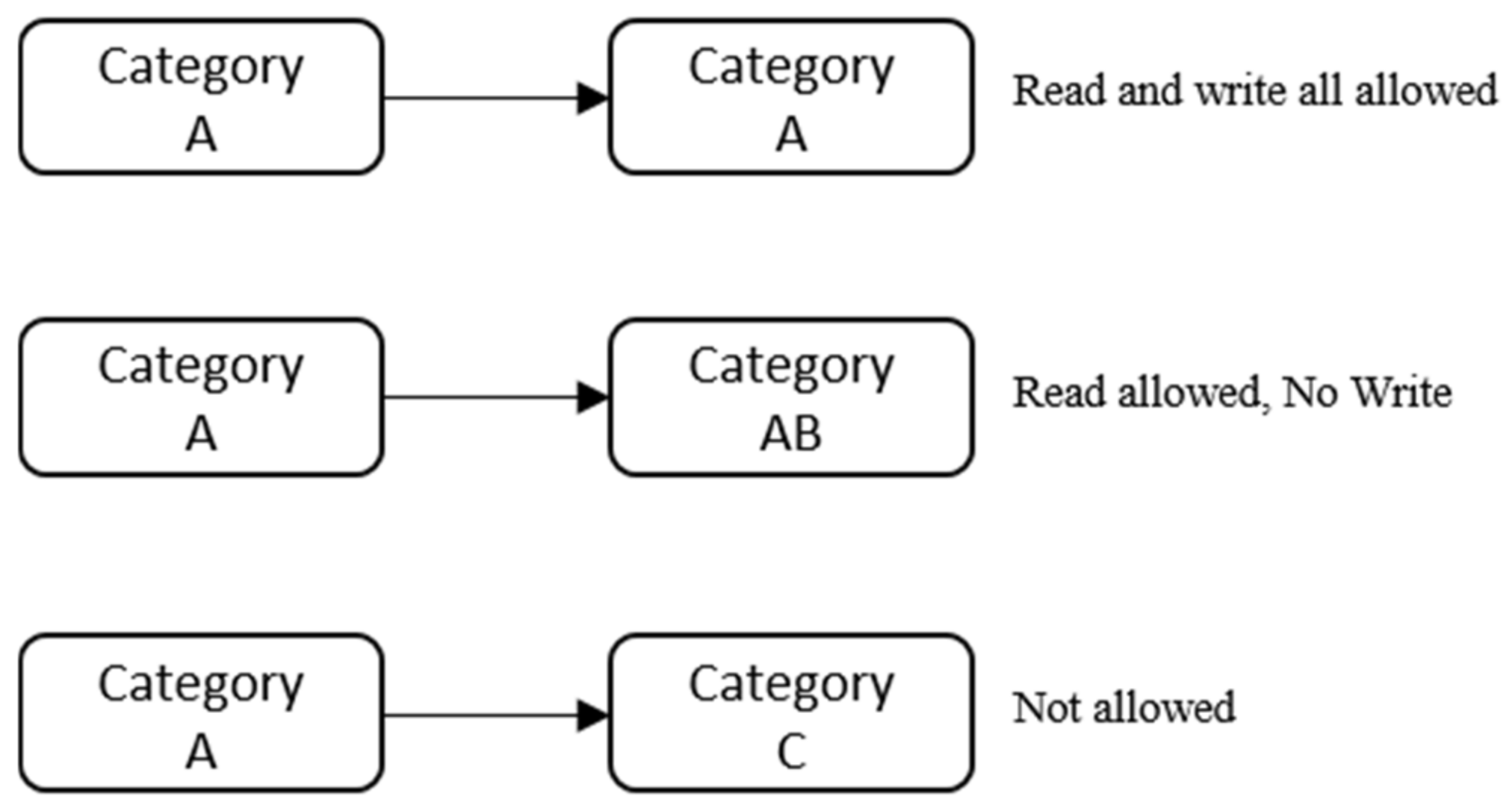
Lattice-based access control - Wikipedia In this type of label-based mandatory access control model, a lattice is used to define the levels of security that an object may have and that a subject may have access to. The subject is only allowed to access an object if the security level of the subject is greater than or equal to that of the object.
Access Control Models - CompTIA Security+ SY0-501 - 4.3 Every object that someone may need to access needs to be assigned a label. It's either confidential, or secret, or top secret, or some other type of label. The users then are provided with certain rights. Certain users can access confidential objects. Other users may be able to access top secret objects.
Using Security Labels for Directory Access and Replication Control - Isode The access control model is that a Security Label is associated with each entry in the directory, and that label indicates the sensitivity of the information contained in the directory entry. The example DIT "organizations", with different Security Labels.
Label Security | Oracle Oracle Label Security records and enforces access permission for data based on project codes, regions, or data classifications. These controls reduce the risk of unauthorized access to sensitive data and help to demonstrate regulatory compliance. Learn more about Oracle Database security. Watch the overview video (8:16)
Define access control list and capability list and compare them ... The Discretionary Security Property: use of an access matrix to specify the discretionary access control. SE Linux, like most other systems that protect multi-level data, uses the BLP model. This model specifies how information can flow within the system based on labels attached to each subject and object.
Control external access to resources in Azure Active Directory with ... In this article. Sensitivity labels help you control access to your content in Office 365 applications, and in containers like Microsoft Teams, Microsoft 365 Groups, and SharePoint sites. They can protect your content without hindering your users' collaboration and production abilities. Sensitivity labels allow you to send your organization's content across devices, apps, and services ...
Label-based access control Security labels are objects applied to rows and columns in order to protect these data, and granted to users to give them access to protected data. Protecting tables at row and column levels Protect rows and columns by associating them with security objects by including clauses in the CREATE TABLE and ALTER TABLE statements. Exemptions

retail security anti-theft 58khz eas soft tag strips sticker am dr label for security door eas am anti theft system(1000 pieces)



!['Mandatory Access Control Essentials with SELinux': Costas Senekkis, ICSI [CRESTCon 2019]](https://i.ytimg.com/vi/h4eG8y53D9Q/maxresdefault.jpg)











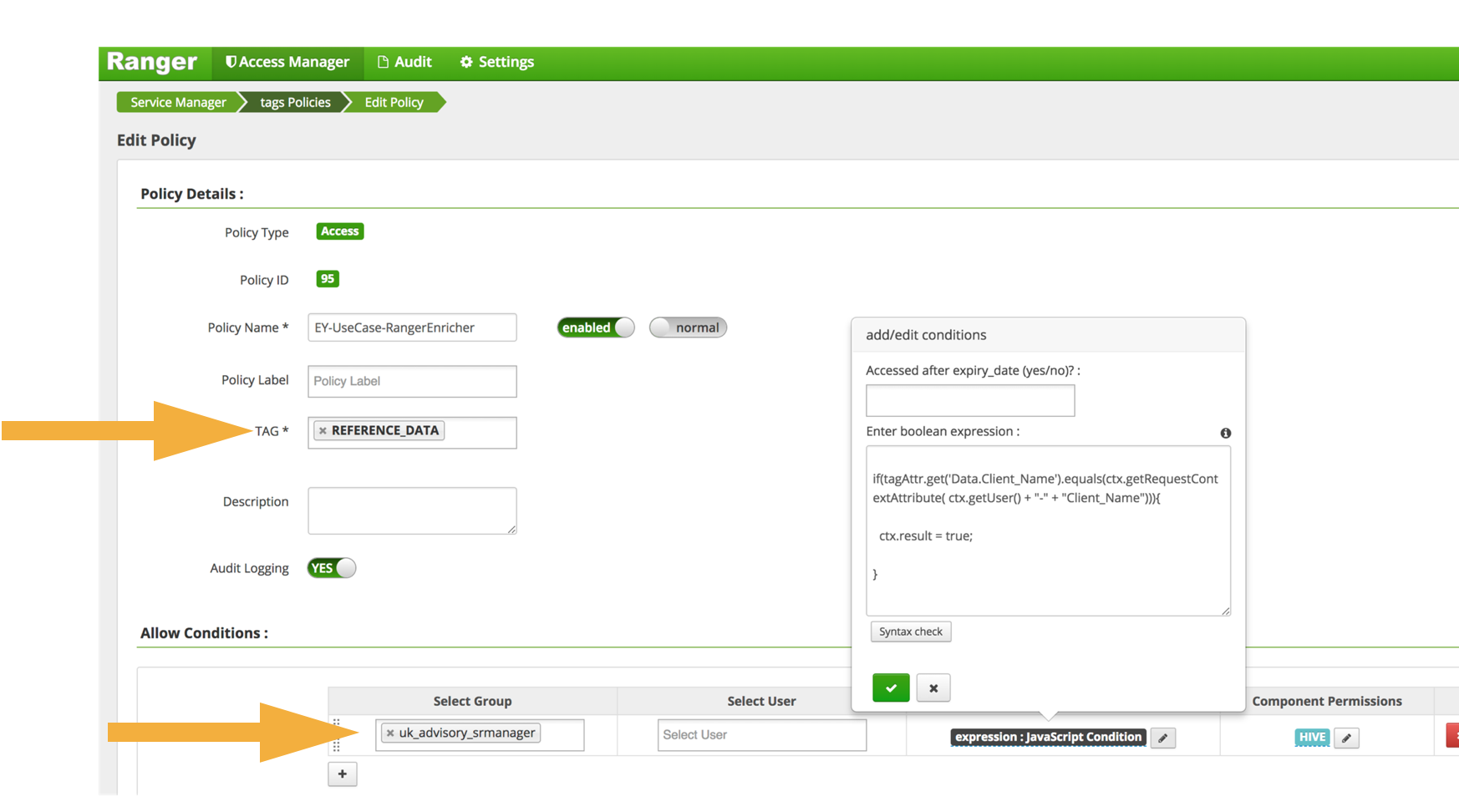
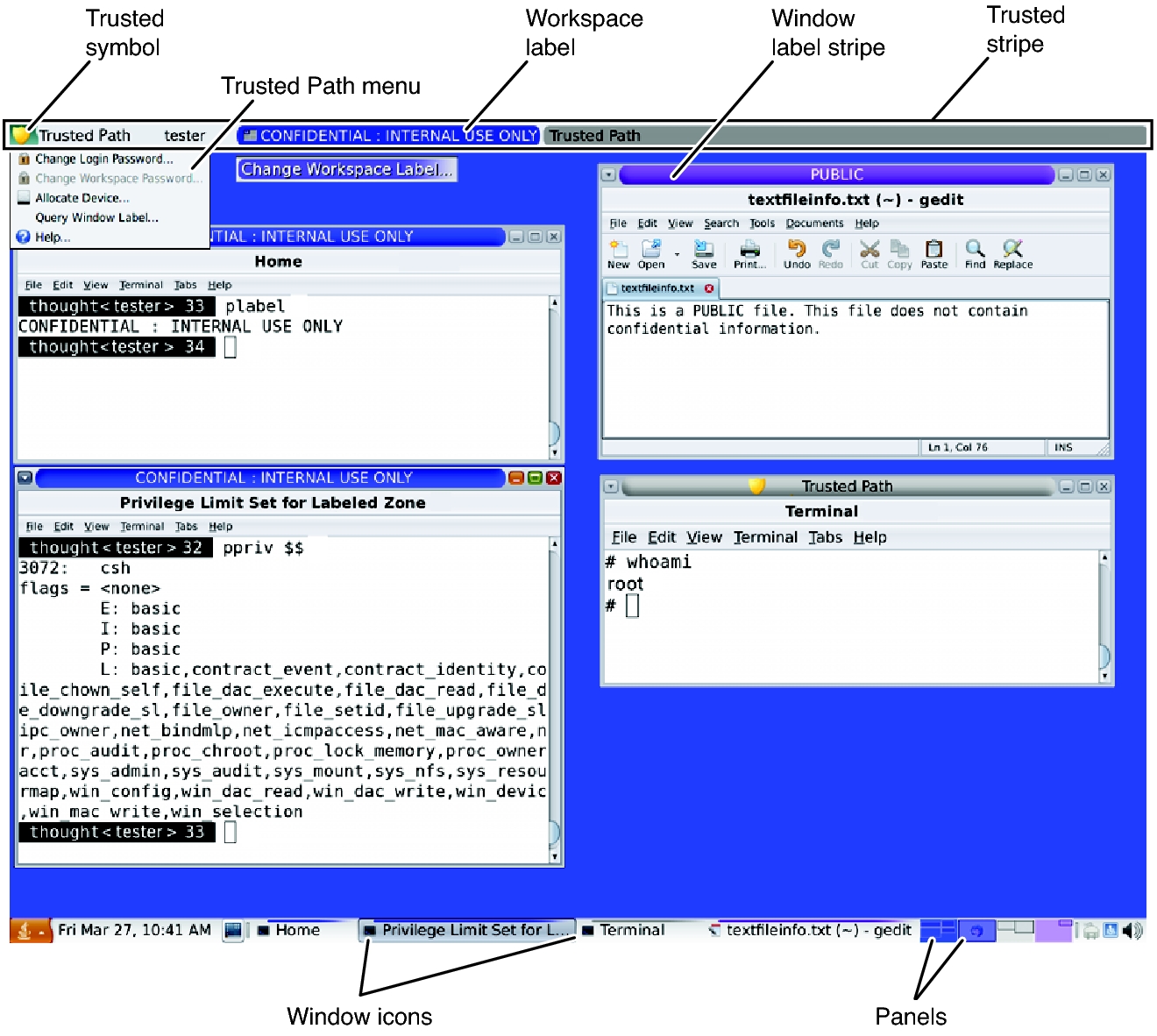
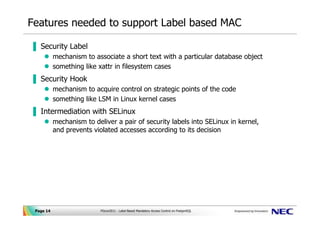


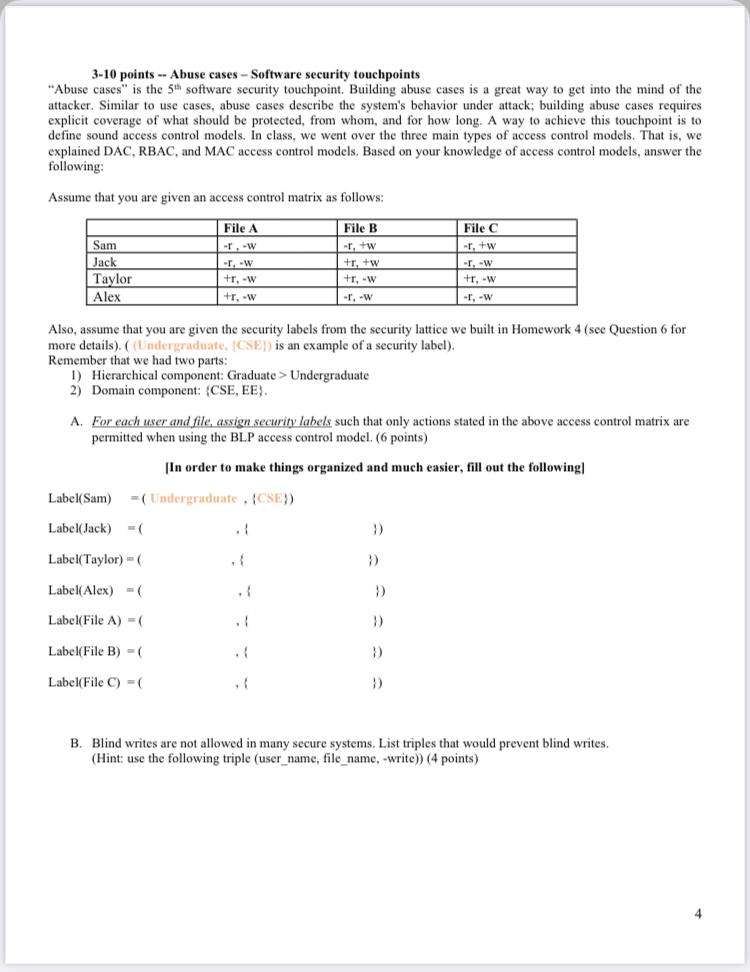








Post a Comment for "42 security labels access control"